Security of Advanced Access Content System
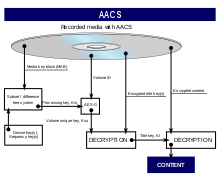
The security of Advanced Access Content System (AACS) has been a subject of discussion amongst security researchers, high definition video enthusiasts, and consumers at large since its inception. A successor to Content Scramble System (CSS), the digital rights management mechanism used by commercial DVDs, AACS was intended to improve upon the design of CSS by addressing flaws which had led to the total circumvention of CSS in 1999. The AACS system relies on a subset difference tree combined with a certificate revocation mechanism to ensure the security of high definition video content in the event of a compromise.
Even before AACS was put into use, security researchers expressed doubts about the system's ability to withstand attacks.
Comparison of CSS and AACS
[edit]| Content Scramble System | Advanced Access Content System | |
|---|---|---|
| Algorithm | Proprietary LFSR-based | AES |
| Key strength | 40-bit | 128-bit |
| Certificate revocation | No | Yes |
History of attacks
[edit]The AACS proposal was voted one of the technologies most likely to fail by IEEE Spectrum magazine's readers in the January 2005 issue.[1] Concerns about the approach included its similarity to past systems that failed, such as CSS, and the inability to preserve security against attacks that compromise large numbers of players. Jon Lech Johansen, who was part of the team that circumvented CSS, said he expected AACS to be cracked by the end of 2006 or the beginning of 2007.[2]
In late 2006, security expert Peter Gutmann released "A Cost Analysis of Windows Vista Content Protection", a technical paper criticizing the implementation of various content protection technologies in Windows Vista.[3]
Providing this protection incurs considerable costs in terms of system performance, system stability, technical support overhead, and hardware and software cost. These issues affect not only users of Vista but the entire PC industry, since the effects of the protection measures extend to cover all hardware and software that will ever come into contact with Vista, even if it's not used directly with Vista (for example hardware in a Macintosh computer or on a Linux server).
Microsoft later claimed that the paper contained various factual errors.[4][5]
While great care had been taken with AACS to ensure that content was encrypted along the entire path from the disc to the display device, it was discovered in July 2006 that a perfect copy of any still frame from a film could be captured from certain Blu-ray and HD DVD software players by using the Print Screen function of the Windows operating system.[6] [7] It was suggested that this approach could be automated to allow a perfect copy of an entire film to be made, in much the same way that DVD films were copied before the CSS was cracked, but to date no such copy has been discovered. This exploit has been closed in subsequent software versions.
Such approaches do not constitute compromises of the AACS encryption itself, relying instead on an officially licensed software player to perform the decryption. As such, the output data will not be in the form of the compressed video from the disc, but rather decompressed video. This is an example of the analog hole.
Both title keys and one of the keys used to decrypt them (known as Processing Keys in the AACS specifications) have been found by using debuggers to inspect the memory space of running HD-DVD and Blu-ray player programs.[8][9][10][11] Hackers also found Device Keys,[12] which are used to calculate the Processing Key, and a Host Private Key[13] (a key signed by the AACS LA used for hand-shaking between host and HD drive; required for reading the Volume ID). The first unprotected HD DVD movies appeared on BitTorrent trackers soon afterwards.[14] The Processing Key for the first Media Key Block version, which could be used to decrypt any AACS protected content released up to that point, was found and published on the Internet at the Doom9 forums. AACS Licensing Authority sent multiple DMCA takedown notices to web sites hosting the key.[15] Some administrators of sites which consist of user-submitted content, such as Digg and Wikipedia, tried to remove mentions of the key fearing reprisals from AACS LA.[16] [17] Both sites' administrators eventually decided to allow publication of the key.[18]
Cyberlink, the company which sells the PowerDVD player, stated that their software could not have been used as part of these exploits.[19]
On April 16, 2007, the AACS consortium announced that it had revoked the Device Keys used by both Cyberlink PowerDVD and InterVideo WinDVD, and patches were made available for users which provided uncompromised encryption keys and better security for the keys.[20] [21] To continue having the ability to view new content users were forced to apply the patches, which also hardened the security of player applications.
On 23 May 2007 the Processing Key for the next version of the Media Key Block was posted to the comments page of a Freedom to Tinker blog post.[22]
The use of encryption does not offer any true protection against memory snooping, since the software player must have the encryption key available somewhere in memory and there is no way to protect against a determined PC owner extracting the encryption key (if everything else fails the user could run the program in a virtual machine making it possible to freeze the program and inspect all memory addresses without the program knowing).
The only way to wholly prevent attacks like this would require changes to the PC platform (see Trusted Computing) or that the content distributors do not permit their content to be played on PCs at all (by not providing the companies making software players with the needed encryption keys).
On January 15, 2007 a website launched at HDKeys.com containing a database of HD DVD title keys. It also featured a modified copy of the BackupHDDVD software allowing for online key retrieval (the latter was later removed after a DMCA complaint).
SlySoft has released AnyDVD HD which allows users to watch HD DVD and Blu-ray movies on non-HDCP-compliant PC hardware. The movies can be decrypted on the fly directly from the disc, or can be copied to another medium. AnyDVD HD is also capable of automatically removing any unwanted logos and trailers. Slysoft has stated that AnyDVD HD uses several different mechanisms to disable the encryption, and is not dependent on the use of compromised encryption keys. They have also stated that AACS has even more flaws in its implementation than CSS; this renders it highly vulnerable,[23] but they will release no details on their implementation. Users at Doom9 claim that the program makes use of the host certificate of PowerDVD version 6.5,[24] but SlySoft has claimed that the program would be unaffected by the AACS revocation system.[25]
Media key block renewals
[edit]This section needs expansion with: missing details, especially media key blocks #13–#64. You can help by adding to it. (December 2022) |
| Version | First titles | Date released | Date circumvented |
|---|---|---|---|
| 1 | The Last Samurai, Million Dollar Baby | 2006-04-18 | 2007-02-13[26] |
| 2 | Never used[27] | ||
| 3 | The Matrix Trilogy | 2007-05-22 | 2007-05-17[28] |
| 4 | Transformers, Spider-Man 3 | 2007-10-30 | |
| 5 | Never used[29] | ||
| 6 | Never used[29] | ||
| 7 | Alvin and the Chipmunks, Aliens vs. Predator: Requiem | 2008-04-06[30] | 2008-04-11[31] |
| 8 | The Forbidden Kingdom | 2008-08-26[32] | 2008-08-26[33] |
| 9 | ? | Approximately 2008-09-03[34] | 2009-03-20[35] |
| 10 | ? | ? | 2009-03-20[35] |
| 11 | ? | ? | ? |
| 12 | Body of Lies, Baraka | 2008-10-09 | 2009-04-06[36] |
| 13 | |||
| 14 | |||
| 15 | |||
| 16 | |||
| 17 | |||
| 18 | |||
| 61 | |||
| 62 | |||
| 63 | |||
| 64 | |||
| 65 | ? | Approximately 2018-06-19[37] | ? |
| 66 | ? | Approximately 2018-11-20[38] | ? |
| 67 | Never used[39] | ||
| 68 | ? | Approximately 2019-03-11[39] | ? |
| 69 | Never used[40] | ||
| 70 | ? | Approximately 2019-07-04[40] | ? |
| 71 | ? | ?[41] | ? |
| 72 | ? | Approximately 2019-10-15[42] | ? |
| 73 | Never used[43] | ||
| 74 | Never used[43] | ||
| 75 | ? | ?[44] | ? |
| 76 | ? | Approximately 2020-04-05[43] | ? |
| 77 | ? | Approximately 2022-06-24[44] | ? |
| 78 | ? | Approximately 2022-08-02[45] | ? |
See also
[edit]References
[edit]- ^ Tekla S. Perry (January 2007). "Loser: DVD Copy Protection, Take 2". Spectrum Online. Archived from the original on 2007-06-08. Retrieved 2007-05-04.
- ^ Johansen, Jon Lech (2006-01-08). "DeAACS.com". So sue me. Retrieved 2007-05-04.
- ^ Peter Gutmann (2006-12-26). "A Cost Analysis of Windows Vista Content Protection". Retrieved 2007-01-28.
- ^ "Windows Vista Content Protection - Twenty Questions (and Answers)". Archived from the original on 2013-01-21.
- ^ Peter Gutmann (computer scientist)#Criticism of Peter Gutmann.27s analysis of Vista DRM
- ^ "Work Around for New DVD Format Protections". Slashdot. 2006-06-07. Retrieved 2007-05-02.
- ^ Edward Henning ("ehe") (2006-07-07). "Copy protection hole in Blu-ray and HD DVD movies". heise Security. Retrieved 2007-05-02.
- ^ "HD-DVD Content Protection already hacked?". TechAmok. 2006-12-28. Retrieved 2007-01-02.
- ^ "Hi-def DVD security is bypassed". BBC News. 2007-01-26. Retrieved 2007-05-02.
- ^ Block, Ryan (2007-01-20). "Blu-ray cracked too?". Engadget. Retrieved 2007-01-22.
- ^ Leyden, John (2007-01-23). "Blu-ray DRM defeated". The Register. Retrieved 2007-01-22.
- ^ ATARI Vampire (2007-02-24). "WinDVD 8 Device Key Found!". Doom9.net forums. Retrieved 2007-05-04.
- ^ jx6bpm (2007-03-03). "PowerDVD private key". Doom9.net forums. Retrieved 2007-05-04.
{{cite web}}: CS1 maint: numeric names: authors list (link) - ^ Yam, Marcus (2007-01-17). "First Pirated HD DVDs Released". DailyTech. Archived from the original on 2007-02-19. Retrieved 2007-05-03.
- ^ "AACS licensor complains of posted key". Retrieved 2007-05-02.
- ^ Boutin, Paul (2007-05-01). "Wikipedia Locks Out "The Number"". Retrieved 2007-05-02.
- ^ Greenberg, Andy (2007-05-02). "Digg's DRM Revolt". Forbes. Archived from the original on 2007-05-04. Retrieved 2007-05-04.
- ^ "DVD DRM row sparks user rebellion". BBC News. 2007-05-02. Retrieved 2007-05-02.
- ^ Lanier, Chris (2007-01-02). "Cyberlink Responds to Alleged AACS Crack". Archived from the original on 2007-06-16. Retrieved 2007-05-02.
- ^ "Press Messages: AACS - Advanced Access Content System". Archived from the original on 2007-04-30. Retrieved 2007-05-02.
- ^ Yam, Marcus (2007-01-26). "AACS Responds to Cracked HD DVD and Blu-ray Disc Protections". DailyTech. Retrieved 2007-05-03.
- ^ "You Can Own an Integer Too". Archived from the original on 2007-08-24. Retrieved 2007-06-09.
{{cite web}}: CS1 maint: bot: original URL status unknown (link) (original link dead) - ^ peer (2007-02-13). "Device key revokation". Slysoft forums. Archived from the original on 2007-09-27. Retrieved 2007-04-09.
- ^ evdberg (2007-02-15). "AnyDVD method of operation". Doom9.net Forums. Retrieved 2007-04-09.
- ^ James (2007-03-02). "And after the process. key is revoked?". Slysoft forums. Archived from the original on 2007-09-27. Retrieved 2007-04-09.
- ^ Thomas Ricker (2007-02-13). "Hackers discover HD DVD and Blu-ray "processing key" -- all HD titles now exposed". engadgethd.com. Retrieved 2007-11-02.
- ^ aKzenT (2007-06-01). "New Processing Key found!! (MKB v3 is now open)". doom9.org forums. Retrieved 2007-11-02.
- ^ Thomas Ricker (2007-05-17). "Newest AACS circumvented: The Matrix Trilogy set free". engadgethd.com. Retrieved 2007-11-02.
- ^ a b "AVP: Requiem/Alvin and the Cipmunks logfiles". Retrieved 2008-04-09.
- ^ "AVP: Requiem/Alvin and the Cipmunks logfiles". Retrieved 2008-04-09.
- ^ "AnyDVD (HD) 6.4.1.1 released". Retrieved 2008-04-11.
- ^ "The Forbidden Kingdom (2008) - MKBv8 - Update server down?". Retrieved 2008-04-09.
- ^ "The Forbidden Kingdom (2008) - MKBv8 - Update server down?". Retrieved 2008-04-11.
- ^ "Blu-ray YELLOW DRAGON'S COLORS Read Error". Retrieved 2009-03-28.
- ^ a b "MKBv9 and MKBv10 Processing Keys found". Retrieved 2009-03-28.
- ^ "Disc using MKBv12 decrypted". Retrieved 2009-04-06.
- ^ "Public MKBs". 2018-06-19. Retrieved 2022-12-22.
- ^ "Public MKBs". 2018-11-20. Retrieved 2022-12-22.
- ^ a b "Public MKBs". 2019-03-11. Retrieved 2022-12-22.
- ^ a b "Public MKBs". doom9.org forums. 2019-07-04. Retrieved 2022-12-22.
- ^ "Public MKBs". doom9.org forums. 2019-10-15. Retrieved 2022-12-22.
… MKBv71 was identical to MKBv70 as far as HRL/DRL …
- ^ "Public MKBs". doom9.org forums. 2019-10-15. Retrieved 2022-12-22.
- ^ a b c "Public MKBs". doom9.org forums. 2020-04-05. Retrieved 2022-12-22.
- ^ a b "Public MKBs". doom9.org forums. 2022-06-24. Retrieved 2022-12-22.
… I found out that MKBv75 does exist. However, HRL/DRL is identical to MKBv72
- ^ "Public MKBs". doom9.org forums. 2022-08-02. Retrieved 2022-12-22.
